Comodo
Endpoint Security

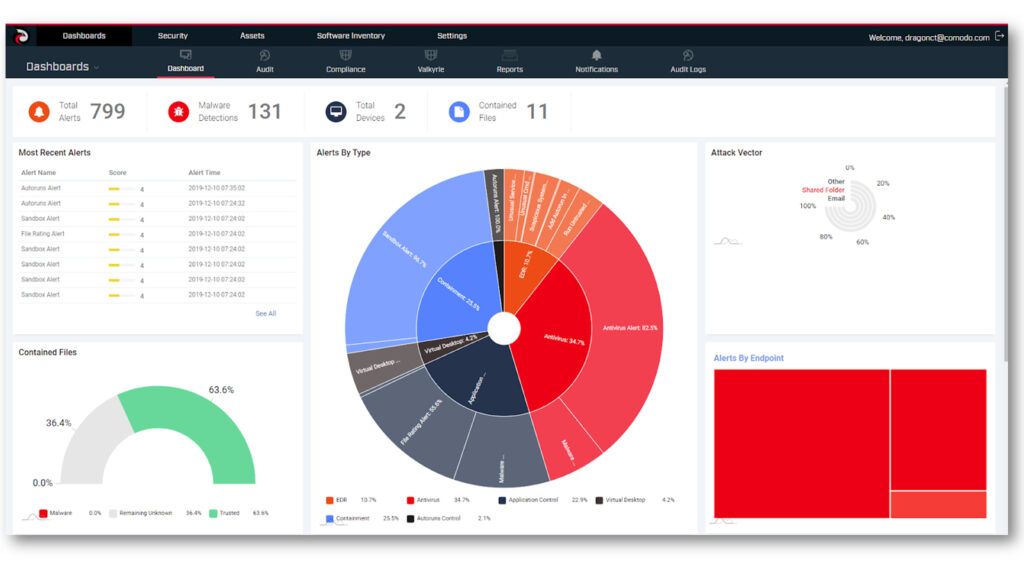
Complete Endpoint Protection With Extensive Threat Hunting And Expanded Visibility
Advanced Endpoint Protection, Endpoint Detection and Response Built On Zero Trust Architecture available on our SaaS EPP.
SECURE YOUR ENDPOINTS FROM RANSOMWARE, DATA BREACHES, & MALWARE
Complete Endpoint Protection Platform Built On Zero Trust Architecture
Complete Endpoint Protection With Extensive Threat Hunting And Expanded Visibility
Analyze your Entire Environment from the Base-Event Level in Real-Time
What Is Managed Detection And Response (MDR)?
Managed Detection and Response (MDR) is an outsourced advanced 24x7 cybersecurity service which is provided by Comodo. We extend threat monitoring and threat hunting from endpoints to network and cloud. Our MDR security experts service your business remotely. You focus on your business.
Network Security

Secure Remote Workforce With Our Cloud-Delivered Security
Users may be digitally savvy, but that doesn't mean they know best when it comes to surfing the internet. As an admin, controlling user web traffic to protect your network and increase productivity can be time consuming.
Email Security To Protect Your Workforce From Phishing Threats And Spams
Our email threat prevention system uses a sophisticated array of spam filters, anti-virus scanners, and content analysis engines to keep spam out while letting legitimate communications in.
Dragon Website Protection
ZERO TRUST ARCHITECTURE
A zero trust security framework is an information technology security model that requires every person and device to first undergo strict identity verification. Users and devices will gain access to the network’s resources once verified.
A castle with high walls surrounding it is an old network security concept. Your network will have a good defence against outside threats. But the biggest threat comes from within the network itself. Migrating to a Zero Trust Architecture is the solution. This will protect your network against both external and internal threats.
In this article, you will learn the benefits of migrating to a zero trust architecture, as well as how to migrate to a zero trust architecture by following the best practices.
Cloud Security

Comodo XDR: eXtended Detection and Response : Discovering Unknowns, Revealing Hidden Threats
Comodo was one of the pioneers of Extended Detection and Response into network (XDR), web and cloud and I guess I am the one to blame as I charted and executed the strategy for this in 2017. A few months later, starting seeing other vendors announcing their NDR solutions, all of a sudden this concept quickly turned into XDR: eXtended Detection and Response. This quick evolution shows the need in the market place. Let me try to explain why EDR was not enough and never will be.
Cloud-Based SIEM

SIEM Solutions for Small Businesses
If you run a small business, it is important to ensure that you boost your network's security. This is mainly because of an increase in not only the frequency of cybersecurity attacks, but also the sophistication of these attacks. Since these attacks usually cause loss of data, erosion of customer confidence, and can even lead to costly litigation, going the extra mile as far as your security is concerned is imperative.
One of the easiest ways to enhance your security is to use SIEM. This is because SIEM provides an easy and highly advanced system of detecting, preventing, and neutralizing security threats. With the enhanced security system that SIEM offers, you will be able to shield your business for the devastating effects of data breaches.
However, not every SIEM solution is created equal. Furthermore, even in cases where a SIEM solution comes armed with powerful security tools, deploying it indiscriminately will limit the benefits that you can get from the system. The following are SIEM tips that will come in handy in ensuring that your business gets the most out of your SIEM.
IT Service Management

What is ITSM?
ITSM involves activities performed by an organization to implement and manage IT services to meet customers' requirements. IT service management is a term used to denote all those activities that any organization today would execute, after proper planning and designing, to control all the IT services.
RMM Definition
Network management software is a type of remote IT management software used by Managed IT Service Providers (MSPs) to remotely monitor client endpoints, networks, and computers. With RMM, MSPs can remotely roll out patches and updates, install and configure software, solve issues, etc.
Service Desk
A service desk is the single point of contact (SPOC) between the service provider (IT) and users for everyday activities. A typical service desk software is capable of managing incidents and services besides handling user communications for things like outages and planned changes to services.
What Is a Ticketing System?
A ticketing system collects and manages all customer support interactions from different platforms, including phone, live chat, email, and social media. This management system enables IT support agents to route various types of tickets to the correct person, resource, or department to obtain the fastest resolution.
ITIL (Information Technology Infrastructure Library)
The Information Technology Infrastructure Library is a set of comprehensive practices that ensures to deliver commending IT services. ITIL has been through multiple revisions and is now composed of five books - each book covers and focuses on a specific set of processes and stages on the lifecycle of IT services.
ITIL was first developed by the Central Computer and Telecommunications Agency of the British Government during the 1980s while it is then first comprised of more than 30 books, that included best practices in IT gathered from various reliable sources from and around the world.
Helpdesk
A helpdesk serves as the contact point for both customers and employees with queries, grievances, and other concerns. While its definition may differ from one organization to the next, there seems to be common ground - that it is used for IT support. Others have used it to refer to customer service or the software used to provide customer support. The bottom line is that it boils down to giving people a chance to seek help.


