Add Your Heading Text Here

In this day and age, devops tools such as Ansible has made it quite possible for security engineers to automate penetration testing. Although it is quite possible to do the same task with bash shell scripting, it becomes tedious when security engineers are supposed to test hosts on different distributions (such as Suse, CentOS and Redhat) . We can use ansible to pentest different Linux distributions in the same environment using playbooks.
Today we will focus on how to install ansible on a controller machine in preparation for the main task ahead. There is no need to install ansible on the remote server ( i.e managed machine) we will connect to shortly.
There are several ways of installing ansible. You can choose to install ansible by compiling source code into the usr/local directory, use apt-get utility of Ubuntu or yum or dnf utility of CentOS to install ansible binary program or install ansible using pip.
For this tutorial, we will install ansible on the controller machine using apt-get and configure it afterwards.
Open your terminal and type the following code:
apt-get install ansible
Usually ansible is installed into the /etc directory. i.e system configuration directory. After you have installed ansible on your Linux machine, type the following command at the terminal:
cd /etc/ansible
Inside the ansible directory, type the command below to view files in the ansible directory:
ls ansible
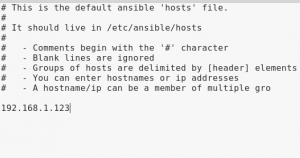
Open the file ‘hosts’ and assign hostname(s) or IP address(es) of remote server you intend to pentest. The ‘host’ file is an inventory file which contains IP address(es) of web servers, database or other infrastructure ansible needs to connect to via ssh. You can choose to open it with any text editor.
leafpad hosts
Now enter the IP address(es) or hostname(s) of remote server(s) in the format below. Please don’t try to connect to the IP address because it is not valid.
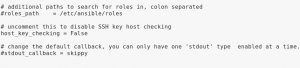
Next, save and close the hosts file. Open the file ‘ansible.cfg’ to make minimal changes. Because we don’t to connect to remote servers passwordless, uncomment host key_checking by ansible by deleting the # sign beside host key_checking
 Now save and close ansible.cfg file.
Now save and close ansible.cfg file.
Finally, let’s check whether we have configured ansible correctly by connecting to remote server using the ping module. The command below simply tells ansible to connect to the ip address(you must replace the place holder with a valid IP address) using the ping module (i.e -m ping). In addition, -k flag prompts user2 for password before connecting to the target.
ansible -m ping -k -u user2
BAM! Ansible is working correctly. Tomorrow, We will illustrate how we can automate information gathering of a target with ansible.
#ISA_informs
#ISA_ltd