Add Your Heading Text Here
To hijack popular Instagram accounts, scammers are sending phishing e-mails with fake copyright infringement notifications.
Have you reached a few thousand followers on Instagram? More? Congratulations, you are insta-famous. Among other things, though, being an Instagram influencer means that it’s quite possible that account thieves are after you. A new phishing scheme targeting popular accounts on Instagram is gaining momentum. Here is how it works.
You’ve got copyright violation notification
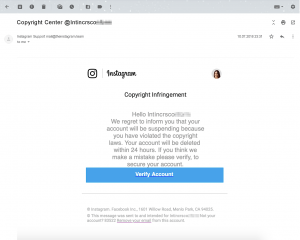
“Your account will be permanently deleted for copyright infringement,” claims an e-mail notification that looks very official. It has the usual Instagram header and logo, and the e-mail address in the From field is extremely close to a legitimate one: In most cases it’s either mail@theinstagram.team or info@theinstagram.team.
The e-mail claims that you have just 24 hours (in some versions it’s 48 hours) to appeal and provides a “Review complaint” button. If you click it, you end up on a convincing phishing page, where fraudsters put an image saying they care very much about copyright protection and offer you a link to “Appeal.” To make the scam look even more legitimate, they offer a long list of language choices, although it doesn’t work — whatever you click, the phishing page always remains in English.
As soon as you click the “Appeal” link, you are invited to input your Instagram credentials. And that’s not the end. Immediately, another message appears: “We need to verify your feedback and check if your e-mail account matches the Instagram account,” it says. Click “Verify My E-mail Address,” and you’ll see a list of e-mail providers. If you choose yours, you’ll be invited to submit both your e-mail address and (surprise!) the password for your e-mail account.
Then, a “We will review your feedback” reply appears, but only for few seconds. After that you’ll be redirected to a real Instagram’s website — another simple trick that lends additional credibility to the scam.
It’s not the first time when Instagram influencers are targeted by scammers. The first wave of phishing was tempting users to apply for a blue “Verified” account badge.








