Add Your Heading Text Here

Today we will look at how ansible modules allows security engineers to check extensive information of a remote server such as active interfaces (i.e eth0, or wlan0), which security feature is implemented inside the kernel ( whether Apparmor or SELinux), how many partition(s) exist on the hard disk and so on.
Although ansible, as a devops tools, is primarily used for configuration management, server provisioning, and application deployment to production environment just like puppet and the rest, some its modules can be used to gather information. Information gathered by ansible modules could be very useful to security engineers.
Before we start to automate information gathering using ansible module, let’s briefly look at how we can get access to ansible modules and arguments related to these modules. To find all modules used by ansible, open the terminal and type the following command: ansible-doc -l 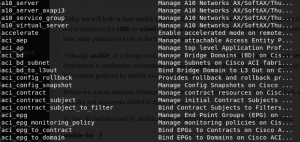
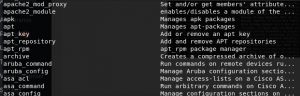
As you can shown in the screenshot above, the previous command we typed at the terminal displayed modules supported by ansible.
Finally, lets use the setup module in ansible to gather information about the target without any infosec tools. Type the command below at the terminal:
ansible -m setup -k -u user2
The command above simply instructs ansible to connect to the target via the IP address provided in the placeholder as user2 and retrieve information related to the target. The -k flag prompts user2 for the password.
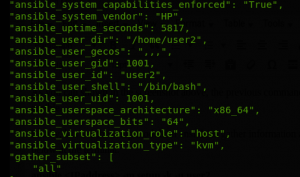
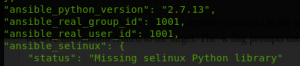
Voila, via the setup module, ansible retrieved extensive information of the target less than a minute. Tomorrow, we will continue to automate information gathering with ansible.
#ISA_informs
#ISA_ltd

 Now save and close ansible.cfg file.
Now save and close ansible.cfg file.
