Add Your Heading Text Here
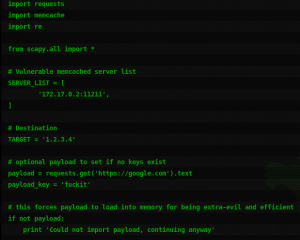
Zenis ransomware is a rare example of crypto-malware. Researchers still cant figure out clearly how this ransomware works. This malware does not only encrypts files but deletes backups too.
Zenis affect devices by exploiting Remote Desktop services. Once inside, it begins to encrypt data using AES cryptography.
Whilst encrypting data, Zenis ransomware renames files and appends Zenis-<2_chars>. file extension. Apart from data encryption, it deletes shadow volume copies, disable startup repair, and clear event logs.
Zenis also searches for files that are associated with backups and deleted them immediately.
Zenis ransomware gets into the machines by exploiting Remote Desktop services connected to the internet directly.
We recommend connecting Remote Desktop Services to the internet via VPN with a strong password. Also, it is quite safer to have anti-malware solution on public-facing machines.
#ISA_informs
#ISA_ltd